验证是否是权限问题。
1.机器首先需要有root权限,执行setenforce 0,执行完getenforce显示Permissive就成功了;
2.修改代码 system/core/init/init.c
bool is_enforcing = selinux_is_enforcing();
+is_enforcing=false;
INFO("SELinux: security_setenforce(%d)\n", is_enforcing); 先模块编译system/core/init/,然后再编译bootimage;
如果以上处理完成后,问题得到解决,则说明是Selinux权限限制导致的该问题;
项目处理:
<38>[ 22.872478] type=1400 audit(1325376041.960:3): avc: denied { read write } for pid=585 comm="system_server" name="au_interrupt" dev="tmpfs" ino=11449 scontext=u:r:system_server:s0 tcontext=u:object_r:device:s0 tclass=chr_file permissive=1
<38>[ 22.896195] type=1400 audit(1325376041.960:4): avc: denied { open } for pid=585 comm="system_server" path="/dev/au_interrupt" dev="tmpfs" ino=11449 scontext=u:r:system_server:s0 tcontext=u:object_r:device:s0 tclass=chr_file permissive=1
<6>[ 23.009953] lowmemorykiller: lowmem_shrink: convert oom_adj to oom_score_adj:1.使用adb shell进入/dev/au_interrupt,执行ls -Z查看此设备的属性设置,此时显示是u:object_r:device:s0 ,对此device进行重新定义;
device\intel\baytrail\sepolicy\file_contexts-->/dev/au_interrupt u:object_r:au_interrupt_device:s0
device\intel\baytrail\sepolicy\device.te-->type au_interrupt_device, dev_type;编译后全部升级,再次进入/dev/下查看ls -Z属性,此时应显示为 u:object_r:au_interrupt_device:s0;
(restorecon /dev/au_interrupt 重新加载属性,然后ls -Z;也可以将此命令写入rc文件)
2.线程名称是system_server,所以进入system_server.te对其进行权限赋值操作;
allow system_server au_interrupt_device:chr_file {read write open};如一行LOG:
<5>[ 17.285600].(0)[503:idmap]type=1400 audit(1356999072.320:202): avc: denied {create } for pid=503 comm="idmap" name="overlays.list" scontext=u:r:zygote:s0
tcontext=u:object_r:resource_cache_data_file:s0 tclass=file即表明idmap 这个process, 使用zygote 的source context, 访问/data/resource_cache 目录,并创建文件时,被SELinux 拒绝访问。
为了规避这种权限放大情况, 我们需要细化访问目标(Object) 的SELinux Label, 做到按需申请.
通常会由三步构成
3.1 定义相关的SELinux type.
比如上述案例, 在 device/mediatek/common/sepolicy/device.te 添加
type tfa9897_device, dev_type;3.2 绑定文件与SELinux type.
比如上述案例, 在 device/mediatek/common/sepolicy/file_contexts 添加
/dev/tfa9897(/.*)? u:object_r:tfa9897_device:s03.3 添加对应process/domain 的访问权限.
比如上述案例, 在 device/mediatek/common/sepolicy/mediaserver.te 添加
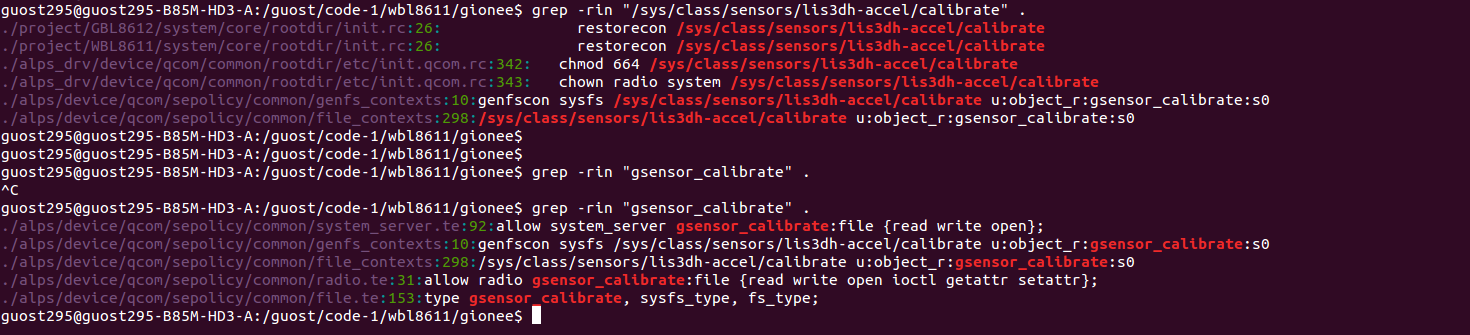
allow mediaserver tfa9897_device:chr_file { open read write };线程system_server和radio访问sys/class/sensors/lis3dh-accel/calibrate节点
以下是dpp2607增加selinux权限的修改
luckstar@luckstar-Lenovo-Rescuer-15ISK:~/work/code/rk312x/device/rockchip/common$ git diff
diff --git a/sepolicy/device.te b/sepolicy/device.te
index 13f7a5f..d6e6c75 100644
--- a/sepolicy/device.te
+++ b/sepolicy/device.te
@@ -26,3 +26,4 @@ type rknand_device, dev_type;
# for sensor device
type sensor_device, dev_type;
+type dpp_device, dev_type;
diff --git a/sepolicy/file_contexts b/sepolicy/file_contexts
index fc55766..901dba4 100644
--- a/sepolicy/file_contexts
+++ b/sepolicy/file_contexts
@@ -48,6 +48,8 @@
/dev/compass u:object_r:sensor_device:s0
/dev/gyrosensor u:object_r:sensor_device:s0
/dev/pressure u:object_r:sensor_device:s0
+/dev/dpp2607 u:object_r:dpp_device:s0
+
# nvm
#/nvm_fs_partition(/.*)? u:object_r:nvm_data_file:s0
/system/bin/nvm_useragent u:object_r:nvm_exec:s0
diff --git a/sepolicy/system_server.te b/sepolicy/system_server.te
index 831fd42..e900ed1 100644
--- a/sepolicy/system_server.te
+++ b/sepolicy/system_server.te
@@ -5,3 +5,4 @@ allow system_server default_prop:property_service set;
allow system_server sensor_device:chr_file r_file_perms;
allow system_server thermal_file:file rw_file_perms;
allow system_server socket_device:sock_file write;
+allow system_server dpp_device:chr_file rw_file_perms;备注:在external/sepolicy/global_macros定义了rw_file_perms
按照以上方法修改后,在eng模式下使用时没有问题的,但是切换到user模式下会报错:
01-21 09:06:44.626 I/SystemServer( 432): Dpp Service.
01-21 09:06:44.650 E/SystemServer( 432): Failure starting Dpp Service
01-21 09:06:44.650 E/SystemServer( 432): java.lang.SecurityException这个时候有两种方法处理,一个是按文章开头说的修改代码取消SELinux的机制,这个时候看logcat信息:
/SELinux ( 158): avc: denied { add } for service=dpp scontext=u:r:system_server:s0 tcontext=u:object_r:default_android_service:s0 tclass=service_manager第二种方法就是按照SELinux机制添加,这个要参考上面方面的log信息:
1.
cd external/sepolicy/
guost@guost-System-Product-Name:~/work/code/code_user/rk312x/external/sepolicy$ git diff service.te service_contexts
diff --git a/service.te b/service.te
index ca461f1..2414c1a 100644
--- a/service.te
+++ b/service.te
@@ -10,3 +10,4 @@ type radio_service, service_manager_type;
type surfaceflinger_service, service_manager_type;
type system_app_service, service_manager_type;
type system_server_service, service_manager_type;
+type dpp_service, service_manager_type;
diff --git a/service_contexts b/service_contexts
index 767d7db..db1fb27 100644
--- a/service_contexts
+++ b/service_contexts
@@ -120,5 +120,6 @@ wifip2p u:object_r:system_server_service:s0
wifiscanner u:object_r:system_server_service:s0
wifi u:object_r:system_server_service:s0
window u:object_r:system_server_service:s0
+dpp u:object_r:dpp_service:s0
* u:object_r:default_android_service:s0
guost@guost-System-Product-Name:~/work/code/code_user/rk312x/external/sepolicy$ 2.
cd device/rockchip/common/
guost@guost-System-Product-Name:~/work/code/code_user/rk312x/device/rockchip/common$ git diff sepolicy/system_server.te
diff --git a/sepolicy/system_server.te b/sepolicy/system_server.te
index e900ed1..639b18d 100644
--- a/sepolicy/system_server.te
+++ b/sepolicy/system_server.te
@@ -6,3 +6,4 @@ allow system_server sensor_device:chr_file r_file_perms;
allow system_server thermal_file:file rw_file_perms;
allow system_server socket_device:sock_file write;
allow system_server dpp_device:chr_file rw_file_perms;
+allow system_server dpp_service:service_manager {add};
guost@guost-System-Product-Name:~/work/code/code_user/rk312x/device/rockchip/common$selinux权限修改,注意device目录和external目录下的同名文件
权限定义文件: system/sepolicy/public/global_macros